Regularly, variants of Emotet pass under the radar of anti-virus software, because they are obfuscated. The ANSSI warned of this situation in the alert bulletin dated September 7, 2020. At Cyber-Detect, we therefore wondered if Gorille was also able to detect Emotet variants.
Emotet is a banking Trojan that has been rampant since 2014. Emotet has evolved and new versions include new spam and malware delivery services. According to the U.S. Department of Homeland Security, the damage caused by Emotet would amount to $1M, making it one of the most expensive malware.
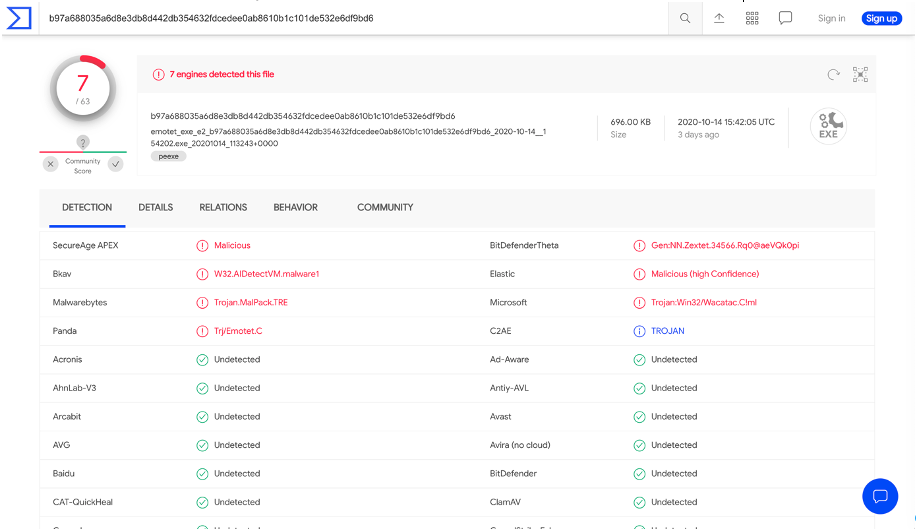
For that, we took the executable whose sha256 is : b97a688035a6d8e3db8d442db354632fdcedee0ab8610b1c101de532e6df9bd6
This executable contains a variant of EMOTET. We submitted it to Virus Total on October 14, 2020. Only seven out of sixty-two anti-viruses on the Virus Total platform detected the presence of malicious code in the executable.
Then, we submitted, this same executable to Gorilla on the site : http://demo.gorille.tech/
In less than a second, Gorille answers that this executable is malicious with a static analysis:
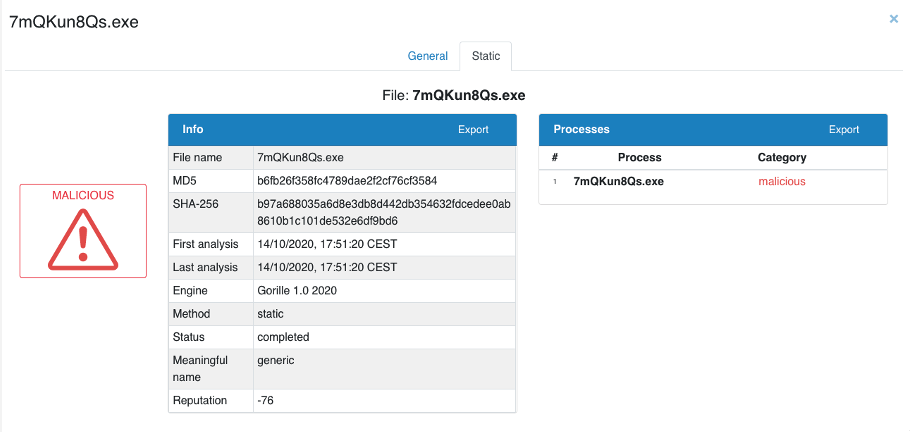
The first conclusion is that Gorille detects this variant of Emotet unlike the vast majority of anti-viruses. This shows Gorille’s ability to analyze weak signals that remain visible despite the protections applied to this sample of Emotet. Gorilla’s morphological analysis engine is able to detect weak signals because it looks for correlations between low-level malicious behavior, i.e., at the executable code level.
To go further, we have performed a dynamic analysis. The static analysis is fast, but does not allow to get past the different obfuscations linked to packers. On the contrary, the dynamic analysis allows to see the different processes that are launched and thwarts many obfuscations, which allows to analyze the load (payload) of the sample.
The result of the dynamic analysis, below, confirms the previous one. The analysis time is about 40 seconds.
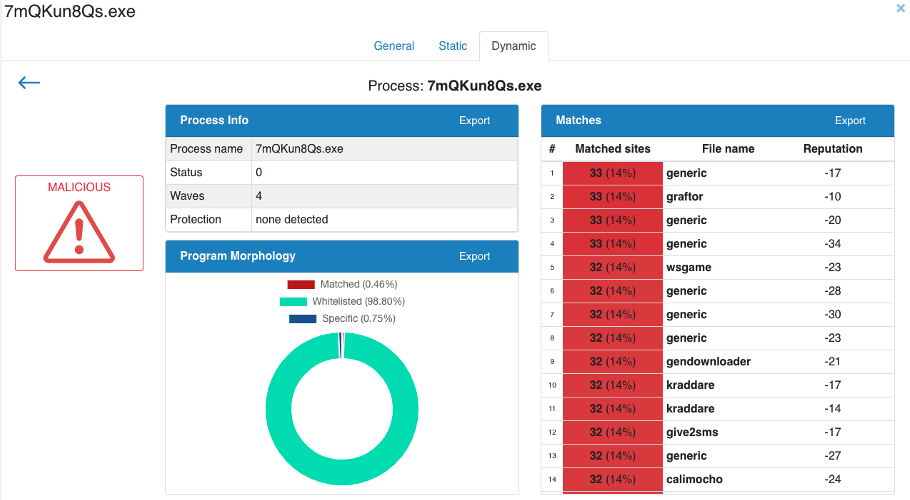
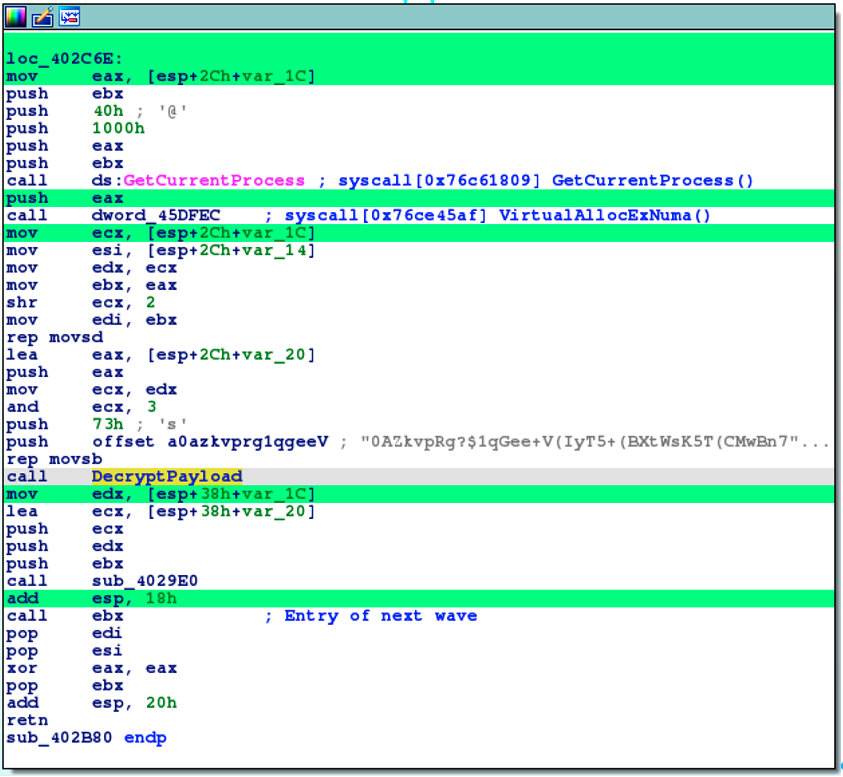
LThe dynamic analysis also shows that this Emotet sample is deployed by depackaging 4 successive waves of code. Each wave of code is analyzed. This Emotet sample contains 33 sites in common with known malicious code. Each of these sites corresponds to a malicious behavior. This triggered the Gorilla alert. Gorilla is also an intelligent reverse-engineering tool. The first wave of code in this sample contains the code of an application that is described by this site: https://www.codeproject.com/Articles/1667/CPJAImage-Yet-another-image-drawing-class/.
The code of CPJAImage has been modified in order to decrypt the program that will allow to install Emotet. The passage from the decryption of the load to its execution is given below:
In conclusion, Gorille’s morphological analysis engine analyzes the behaviors of submitted binary files and overcomes the various protection measures that hide the intent of the analyzed file. The case study presented here with a variant of Emotet, undetected by most Anti-Virus software, demonstrates the effectiveness of Gorille.