When it comes to cybersecurity, using an EDR has become a prerequisite. Indeed, it is a full-fledged cyber defense component to protect its workstations.
According to the military approach, building or using a cyber defense capability means mobilizing capabilities known under the NATO acronym “DOTMLPFI” :
The main added value of these capabilities is that they are based on anticipation.
These cyber defense capabilities are based on:
- Open or classified sources,
- Historicals,
- Knowledge,
- Contextualization (J6*),
- Analysis management,
- Aggregations,
- Partial or systematic remediation scripts,
- Expertise and participation in the definition of operations (J5/hot plan) and their implementation (J3).
The current focus is naturally on automated software solutions (Materiel for the NATO acronym), such as probes, analysis, orchestration, etc. drastically saving time and human resources, when possible.
These solutions are supposed to scale up (or scalable) and thus compensate for the long and manual processes of reverse engineering. However, time is often of the essence in case of an attack or alleged attack without really knowing the nature of the attack.
Thus, market solutions have been developed to help analysts, whether they are internal or external (MSSP SOC, SAAS, crisis management, subrogation, delegation, etc.).
These solutions are illustrated in the Gartner Group diagram called “TRIAD”. We have expanded it slightly to include other organizations that cannot be automated but are essential to the cyber defense process:
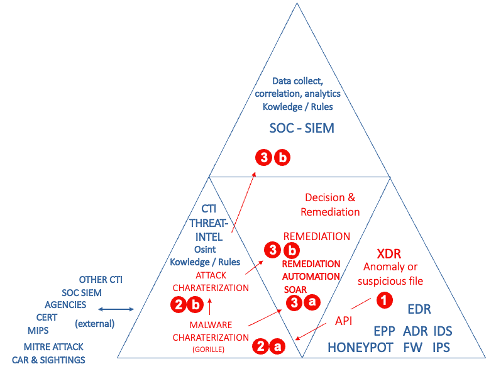
The role and interest of an EDR
TRIAD distinguishes between tools grouped under the acronym “EDR*” whose installed and configured agents are able to isolate a file and present it to other analysis tools. Among the latter we have EPP (EndPoint Protection or classic signature-based AV), behavioral analysis tools based primarily on artificial intelligence (AI).
These tools have to deal with both known viruses (signature database) and unknown ones, descended from sophisticated malware, in variant form. By passing under the radar of these detection tools, these threats settle on the IS, remain dormant and are activated according to the attackers’ triggers.
The response to these attacks can be broken down into 3 steps: detection, malware characterization, and attack characterization.
Malware detection :
By abuse of language, detection takes over the rest of the analysis chain. Detecting is indeed a necessity that must be combined with characterizing the malware: knowing its nature, its action, its technical objective (wiper, ransomware, data-leaks, espionage, etc.), but it is insufficient. It is also necessary to characterize the threat in order to guarantee optimal protection.
Malware characterization :
Malware analysis tools have to deal with 4 protection techniques implemented by attackers: obfuscation, self-modifying encryption and anti-debug measures.
This incident handling segment is critical. It is at the core of the ITC*’s responsibilities to support analysts in the event of an attack. However, detection and characterization are time consuming, costly and reduce efficiency.
Attack characterization :
It relies heavily on well-managed malware characterization, which facilitates thorough research and provides optimal incident response at low cost.
Searching for IOCs, correlations or effects from a detection is risky and delays knowledge and incident response resources.
Gorille® as an extension of its EDR
Beyond the technical aspect, it is necessary to carry out a debriefing on the situation of the attack(s), the infrastructure, the residual risks and to anticipate the other aspects of the handling of the incident (legal aspect, contractual responsibilities, etc.). This consists of exposing a situation and its probable evolution, this is situational awareness.
The market of cyber defense solutions is emerging, it draws its legitimacy both from each internal engine but also from the interoperability of several solutions forming a platform. It is essential to go beyond the traditional antivirus solutions and AI-based probes and turn to an innovative solution: morphological analysis.
By characterizing a threat by its behavior and not only from a malware database, morphological analysis offers a unique accuracy on the identification of viruses and their variants. This analysis does not require a learning phase and can be materialized in the form of control flow graphs to precisely visualize the malicious strains of an executable file. This technology is embedded in the Gorille® solution engine.
Using morphological analysis, Gorille® Cloud has the ability to provide complete and instant characterization to inform analysts about the attack. It also integrates within an xDR* platform and targets endpoints, servers, but also incoming files and the supply chain.
Adopting Gorille® within an EDR platform guarantees a relevant and rapid analysis, and in 99% of cases, an automatic treatment of the incident. This avoids overly constrained tuning, risking blocking user workstations or production servers without justifying the nature of the attack and its repercussions.
To conclude,
Pairing Gorille® with an EDR means reducing your risks and minimizing your exposure to future claims. It also means keeping the possibility of negotiating its guarantee premiums by displaying good practices with a breakthrough tool.
The use of Gorille® acts on the four risk mechanisms that are :
- probabilities of attack occurrence, deployment on the network and endpoints,
- the threat already described above that would fly under the radar,
- the vulnerability of cyber defenses,
- the effects in terms of loss of business, penalties, civil liability, etc.
GLOSSARY :
DOTMLPFI*
Doctrine, organization, training, materials, leadership and education, personnel, facilities and interoperability: The term refers to several distinct actions (https://www.nato.int/cps/fr/natohq/official_texts_156374.htm?selectedLocale=fr)
J3*. Operation (definition of actions, their sequences, their conduct). Defined as a long term need (cold plan) or short term need (hot plan). See J5.
J6*. Information from all sources.
J5*. Short and long term planning of capacity building.
CTI*
Cyberthreat Intelligence or Anticipation. Sources and means of analysis of attacks, whatever their timing (tactical, operative or strategic).
xDR*
Regroups the so-called (E)ndpoint (D)etection and (R)esponse solutions in the form of an agent installed on the terminal, as well as (A)DR for Application Detection and Response, the best known of which are those that process horizontal or vertical/business mails (Application). These agents scan the actions of the executable binary on the computer and isolate a suspicious file.
Risks*
4 properties: threats (malware), vulnerability, probability, effects and time axis one.
Status Report*
This involves reporting at several communication frequencies to give an idea of the attacks, their evolution, the state of the production and support systems (IS), the anticipation and the palliative operational solutions.