Emotet is a banking virus that has been rampant since 2014 and is one of the most costly according to the U.S. Department of Homeland Security on par with Ryuk or TrickBot malware. Present in an email or in a booby-trapped link, Emotet sneaks into fake invoices, shipping notices or even health information linked to covid-19.
The Emotet Trojan is a dropper. After infection, a dropper has the function of installing the payload. Thus, the Emotet dropper can install other ransomware and completely infect an endpointy.
New variants of the Trojan are constantly being identified, which makes it even more difficult for the majority of antivirus software on the market to detect.
On September 7, the ANSSI published an alert on the Emotet virus because its damage, in France and in the world, had already reached more than one million dollars.
In October 2020, only seven out of sixty-two anti-viruses were able to identify the present malicious code.
On January 18, 2021, a new variant of the Trojan was submitted to the VirusTotal site, which aggregates 68 antivirus programs. However, only 33 of them, or less than half, detected this variant. The detection of Emotet is crucial, as it signals the beginnings of an attack with serious consequences, and this detection must happen as soon as possible.
Why do variants of the Emotet dropper escape antivirus software? Even those based on artificial intelligence techniques, while Emotet has been around for several years? The reason is that each variant incorporates a new camouflage of the dropper and in the case of this Emotet variant, the original program is hidden in free code. As a result, a majority of antivirus programs are fooled.
How to detect this variant ?
Despite the effectiveness of antivirus software, it is advisable to use a complementary solution that detects, classifies and analyzes variants of known malicious code, but also unknown threats. The answer lies in morphological analysis. This method allows to gather and link known and unknown malicious behaviors in order to assemble, in less than a second, all the pieces of the puzzle. In order to avoid “false positives”, morphological analysis will exhibit similar behavior already identified in known malicious code and thus infer that the correlation of behavior can lead to a malicious action. The best morphological analysis solutions offer the possibility to manually verify the system analysis. In the case of the Emotet variant, the variant was camouflaged in the free software Clipping Regions , and the code portion in this Emotet variant from memory address 0x10002365 contains the real Emotet execution code.
Demonstration in pictures:
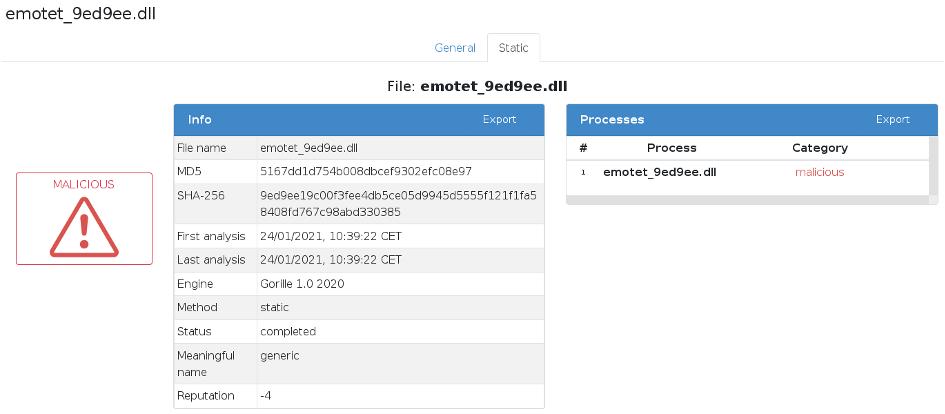
By asking for more information, the morphological analysis specifies that this file has a malicious behavior and that this feature was already present in another malicious code whose MD5 is given.
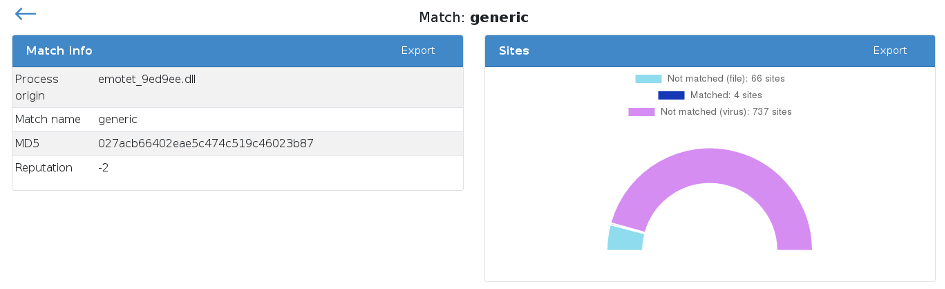
Thus, the variant is correctly detected, outperforming the majority of the antiviruses present on the Virus Total site.
To go further:
With new malware variants blooming faster than the buds in spring, it is now necessary to use morphological analysis to ensure effective protection against cyber attacks. Whether these attacks are sophisticated, targeted or simply not yet detected, the majority of antivirus solutions are not sufficient to defend against them. Indeed, although antivirus software covers 99.9% of current viruses, the remaining 0.01% are responsible for 95% of the damage caused by cyber attacks. Thanks to its sub-second response time, the exploration of malicious behavior contained in morphological analysis is an effective and rapid solution against unknown malware.
Contact us :
The Cyber-Detect R&D team at the origin of the morphological analysis solutions answers your questions: contact@cyber-detect.com